Phishing Awareness Emails Sent to Employees
Phishing continues to challenge the security efforts of businesses worldwide. This seemingly simple yet highly effective method of entry into a corporate network will often focus on specific employees and exploit their behavior. The result of successful phishing attacks can cost businesses enormous amounts of time and money. This was recently experienced by a finance department employee at a small Ohio city; the employee was a victim of spear phishing as part of a Business Email Compromise (BEC) Scam. The employee handed over almost $219,000 to the scammer after being convinced they were paying money into a legitimate supplier account.
Phishing awareness emails are vital for training employees to prevent incidents like BEC scams. Here are some facts about phishing and how to use phishing awareness emails to train employees.
Did You Know?
in phishing susceptibility with SafeTitan
of employees share passwords
estimated global cybercrime cost
of data breaches involved a human being
Phishing Statistics
Understanding the volume and impact of phishing helps justify using security awareness and phishing simulations. Show employees the effects of phishing and how common it is by creating fact sheets showing where attacks happen, the impact of an attack, and the costs of dealing with the aftermath of a phishing attack.
Here is some of the latest research detailing the serious nature of phishing:
-
The Anti-Phishing Working Group (APWG) 3rd Quarter 2022 report identifies 1,270,883 phishing attacks for the quarter. This is the worst quarter for phishing ever observed by the APWG.
-
The AWPG report pulls out Business Email Compromise (BEC) attacks as a core reason for phishing attacks, with the number of BEC attacks in Q3 increasing by 59%.
-
Worryingly, “advance fee fraud” scams that are initiated using phishing emails increased by 1,000% in Q3.
-
Figures such as these are backed up by further research from the likes of industry stalwarts, IBM, that are based on real-world threat-gathering exercises. For example, the IBM 2023 Threat Intelligence Report found that 27% of all cyber-attacks were extortion related, for example, BEC fraud.
-
The IBM report also points out that the top vector for a cyber-attack remains phishing, with 41% of attacks relying on phishing to begin an attack chain.
-
The October 2022 ENISA Threat Landscape Report concurs with IBM’s findings, adding:
Phishing is once again the most common vector for initial access. Advances in sophistication of phishing, user fatigue and targeted, context-based phishing have led to this rise.
Types of Phishing
There are many types of phishing, and as time passes and more is known about each class, fraudsters innovate and invent new forms. Here are some of the most found phishing types in circulation:
- Clone Phishing
- Barrel phishing
- Executive phishing/Whaling
- Domain Spoofing
- Spray email phishing
- Spear phishing
- Smishing (mobile text message phishing)
- Vishing (phone call/voice phishing)
- Social media phishing (social posts used to carry malicious links to spoof websites)
27% of all cyber-attacks were extortion-related, with phishing being the top vector for initiating these attacks at 41%.
Three Real-life Phishing Emails
Three real-life phishing emails demonstrate the type of methods used to exploit employees. The three examples, taken from real life, include some of the most common tactics:
Phishing Email 1: Barrel Phishing with Fake Invoice
Invoice scams are often part of Barrel phishing attack, which uses a double-email ruse to trick employees. Usually, these scams will be focused on employees who deal with licensing or accounts payable. In the example below, the fraudsters have used specific tactics to gain trust and ensure a successful phish:
- Well-known brand: the scammers have used Norton security software to trick the employee into believing the email is legitimate. Norton has around 80 million customers worldwide, so the target company will likely use the software.
- Trust established: the email states that payment has already been made, but a follow-up email will be sent. This second email will be malicious.
- Malicious link: the second email will contain a link to a spoof website. By now, the target will be keen to check the invoice payment; they may even think it is a mistake. If they click the link and navigate the website, they will be asked to enter login credentials and/or personal and financial data, which the fraudster will steal.
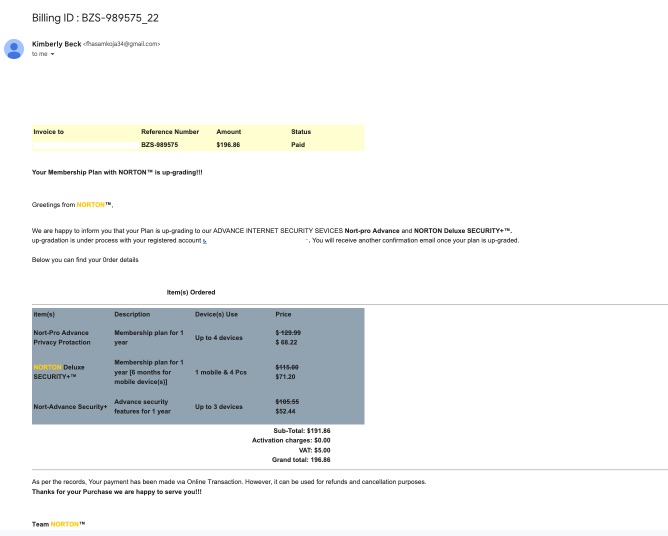
Barrel Invoice scam email
Phishing Email 2: Outlook Fake Upgrade Email Scam
Microsoft is also one of the most spoofed brands used to trick employees during phishing attacks. The Outlook fake upgrade scam is a regular phishing attack that uses a variety of behavioral manipulation techniques, including:
- Well-known brand: Microsoft is well-known and used by many millions of companies worldwide; employees regularly receive Outlook emails from administrators.
- Sense of duty: the upgrade scam depends on an employee’s wish to do a good job and comply. In this example, they say that all staff is “expected” to migrate to the new version of Outlook.
- Sense of urgency: the email limits 24 hours to upgrade or risk losing email access.
- Fear and uncertainty: the email plays on concerns over continued access to pay slips and other important documents unless the recipient clicks a link to upgrade.
- Malicious link: the email contains a malicious link that will take anyone clicking it to a spoof landing page where the fraudsters will attempt to gather Outlook login credentials to use with the real Outlook account.
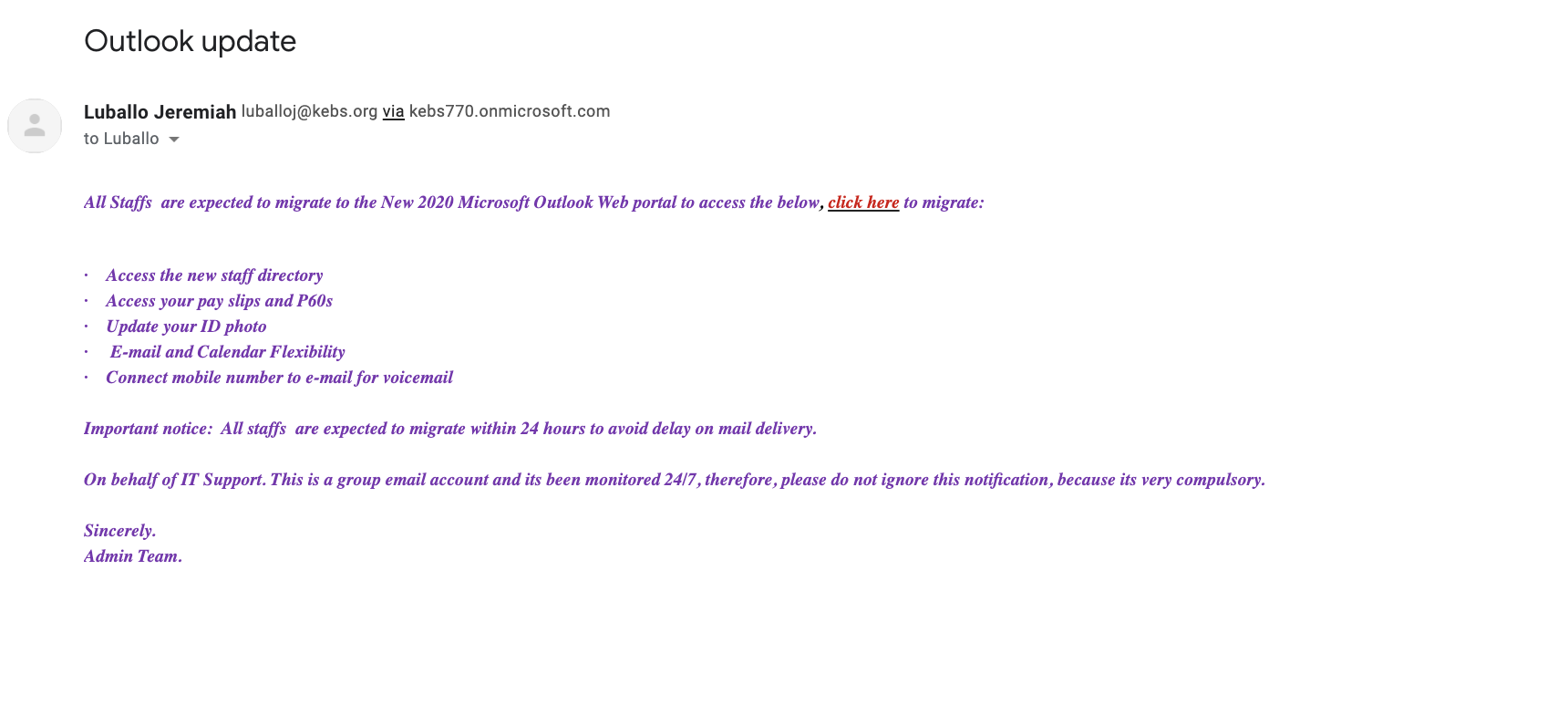
Outlook update scam
Phishing Email 3: Infected Attachment Scam
Fraudsters often attempt to infect a device using a malicious attachment in a phishing email. Attachments may be disguised as invoices, important company documents, or voice messages. In this example, the message has an attachment that is presented as a text message sent from a mobile device.
- Curiosity: the type of behavior that this scam manipulates is a sense of curiosity. The scammer is hoping that the recipient will be intrigued enough to click to open the message.
- Infected attachment: malicious attachments come in many forms. If the recipient clicks to download or open the attachment, this action will activate the malware. This malware will exploit software flaws that are present in your device and install malware: the malware may be ransomware, or it could steal login credentials and other data.
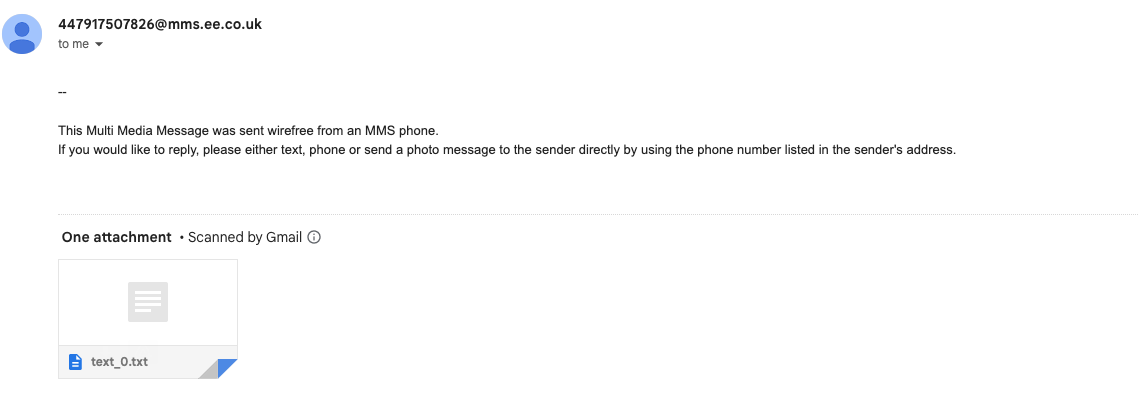
Infected attachment
Ideas for Phishing Simulation Exercises
Phishing simulation is a great way to teach employees about the tricks that fraudsters play when using phishing emails. Advanced phishing simulation platforms are designed to replicate current and potential threats that scammers use to target a business. Advanced systems, such as SafeTitan, provide phishing templates that can be used to generate realistic phishing emails to send to employees, business contractors, suppliers, and other stakeholders. Additionally, advanced simulated phishing solutions, such as SafeTitan, deliver tailored sessions that mimic specific threats targeting departments and individuals. However, unlike real phishing emails, the simulated phishing exercises are done under controlled conditions that reinforce and educate to ensure that trainees know how to spot phishing attempts.
Here are some ideas for phishing simulations to send to employees and other business stakeholders.
Phishing The Finance Department
A financial department is attractive to fraudsters because the team members manage company money. Therefore, you should assume that anyone in the finance department is at risk of BEC scams; these phishing scams attempt to harvest login credentials or trick employees into paying spoofed invoices. Again, the two-email Barrel phishing scam will influence this phishing exercise.
- Create two fake emails that target finance team members:
- The first email will be an initial email that attempts to build a rapport with the individual. Make the email jovial and light, and let the recipient know they will receive a second email soon.
- The second email should contain a malicious link that takes anyone clicking on it to a spoof landing page.
- Create a spoof landing page: simulated phishing solutions, such as SafeTitan, will provide a spoof landing page and templates to generate spoof emails. The spoof landing page will attempt to capture the employee’s login credentials.
- Record the activity during the simulated phishing exercise: capture how the employee reacts to the phishing messages. SafeTitan offers Contextual learning as employees perform actions during the simulation. This helps to train users.
Learning outcome: employees should understand that sometimes fraudsters will attempt to build trust by using a sacrificial email to create a relationship before sending a malicious email.
Infected Attachment Exercise
Ransomware infection is commonly carried via an infected attachment. Perform a simulated phishing exercise across all employees and business stakeholders that tests ransomware phishing resistance.
- Create a fake email containing a spoof-infected attachment: SafeTitan provides thousands of phishing templates that have built-in spoof attachments. Ensure that this email reflects current threats, for example, an invoice or voicemail message.
- Manipulate employee behavior: use typical behavior exploits in the email, such as manipulation of an employee’s:
- Sense of urgency.
- Urge to do a good job.
- Sense of curiosity.
- Fear of missing out or losing important information.
- Record the activity during the simulated phishing exercise: capture the metrics on employee reaction to the phishing messages. If the employee attempts to open the attachment, the phishing simulation software should provide contextual learning to show the user what would happen if this was a real infected attachment.
SafeTitan Phishing Awareness Emails for Employees
SafeTitan provides security awareness training packages that include a simulated phishing platform. SafeTitan allows spoof phishing emails to be created from a library of thousands of templates so that you can carefully tailor them to reflect real-world threats on a per-role or per-department basis. SafeTitan captures dynamic metrics to assess the reaction to a simulated phishing email so that this tailoring becomes highly targeted and effective. Some of the core features of SafeTitan, such as real-time behavioral tracking and contextual learning, ensure that phishing awareness emails sent to employees work to educate your user base. Phishing may be the number one vector to infect organizations with ransomware and steal login credentials. Still, advanced phishing simulators such as SafeTitan make these scams much more challenging to execute.
For a demonstration of the power of SafeTitan for phishing awareness emails, book a free demo.

J.P. Roe
- SECURITY AWARENESS TRAINING
Talk to our Team today

