This latest phishing scam is a fake claim that a person’s Netflix account is in danger of being cancelled. The email asks the target to visit a bogus URL to continue using the Netflix service. At the URL they are asked to enter their account details. If the users Netflix email address and password are entered on this page, the scammers will get access to the victim's Netflix account details as well as any other on line accounts using the same credentials. Do you use the same password across various accounts and online services?
62.27million Netflix users - an attractive broad audience for scammers!
TitanHQ advises the best course of action is to ignore the email and not click on it. Customers with concerns should check their account details and contact Netflix directly rather than use any information provided in the email. At the end of Q1 2015 Netflix report the total number of users worldwide grew to 62.27million. With such a large user base it’s an obvious audience for scammers to target.
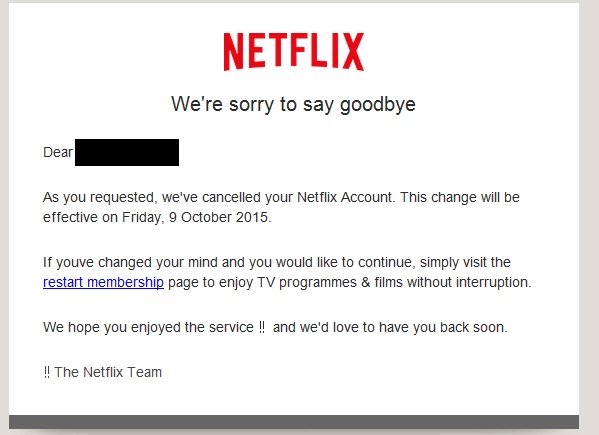
Taking a closer look at this scam email it’s obvious the grammar in the email is not perfect. But it's good enough to fool some people. Not all Netflix users will have perfect English or notice these grammatical errors.
In extracting this personal information scammers will always have a credible excuse for requiring you to handover this information, such as:
- Upgrading security levels
- Essential System maintenance
- Verifying your account details
- Protecting you from fraud
- Offering you a refund for a fee or a bill paid or overpaid
The main goal of most malicious programs distributed via mail is to steal confidential data. The majority of phishing attacks targeted email accounts. Users are often lax when it comes to their email accounts: many of them use simple logins and passwords.
With this kind of attack someone has to be persuaded to open the malware or follow a phishing link. Attacks typically fall into one of three categories:
- Most attacks are opportunistic – people using off-the-shelf jacking toolkits against thousands of networks world-wide. Typically, this involves sending out millions of spam with the hope that someone with follow a link and thus get infected. The ransom-ware malware of the last couple of years would fall into this bracket.
- Use of day-zero vulnerability distributed in a way similar to above. The skill level of the hackers is much higher however their target ‘audience’ is still cast quite wide.
- Finally, targeted attacks against specific organizations utilizing a high-skill level (usually employing a day-zero vulnerability). These advanced persistent threats (APT) are what would have been employed by the authors of the recent Carbanak malware.
How to avoid being phished :
- It’s crucial to stay on top of patching; patch all operating systems and applications. The plethora of patches being released by the various vendors can be quite overwhelming. Organizations need concise patch management practices.
- Continuous security audits, as well as layered network security and best practice education for all employees. Education for employees on phishing emails is essential.
- Never open an email or click a link on a email that you weren’t expecting
- Always hover over links and see where the link points to before clicking on any link.
Technology is essential, but it's not a cure-all solution. There is a massive need to train users to be more alert. No matter what email server or spam filter your company is using there are a few quick and easy things you can do to reduce spam and related malware attacks on your network. Take a look at this checklist ‘ 11 ways to reduce spam and malware attacks’.
Talk to our Team today



