While phishing and ransomware still top the most prominent cyber-attacks, a new trend in malware involves “fileless” attacks. Files used in these attacks can’t execute any significant payload on their own, but instead use a technique coined “living off the land binaries” (LOLBins). Because files need binaries to deliver a payload, the attack uses several steps to download necessary executables to function, usually involving native shell and scripting tools to pull malicious content from the Internet to the local device.
Nodersok Campaign and Node.js
The most prominent of fileless attacks is Nodersok. Nodersok initiates by tricking users into downloading an HTA file. HTA files are older Windows-based HTML applications used to envelop custom web pages within an Internet Explorer instance. The advantage was that the user could run VBScript and other local files within a browser. These applications are relatively outdated, but Nodersok takes advantage of user propensity to download files with extensions that seem harmless.
Once the HTA file is downloaded, Nodersok performs several steps in an elaborate way to avoid anti-malware systems. It uses JavaScript in the HTA application to download additional files, and then uses the Windows shell application PowerShell to eventually download Node.exe. Node.exe is the Windows variant of the Node.js framework. The Node.js framework turns any machine into a proxy, which is the goal for the Nodersok malware. After successful infection, Nodersok uses its proxy capabilities to perform click fraud. By having users silently click on advertiser ads, the malware creator earns money in fraudulent clicks that seem like valid traffic to the ad network.
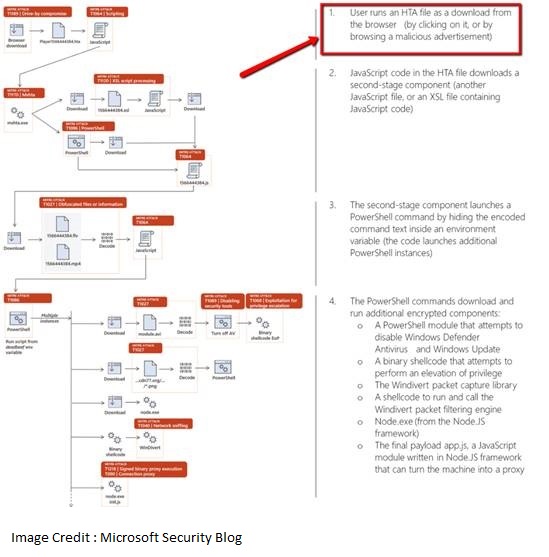
Using native tools is what makes this latest fileless malware attack an innovative new trend for attackers. It also makes detecting the attack much more difficult for anti-malware applications due to the “harmless” nature of the original file downloaded by the user. Additionally, Nodersok uses PowerShell to disable antivirus applications to avoid detection. Microsoft reports that most attacks focus on consumers, and the latest campaign wave targets mainly devices in the United States and Europe.
Protecting Corporate Devices
Because Nodersok disables local anti-malware tools, it’s difficult for corporations to control widespread device infections. The first step in the attack is basic phishing and tricking users into downloading the malicious HTA file. User training helps stop these attacks and provides users with the right education to identify attacks and notify IT staff, but it takes only one user to spread the malware across several corporate devices. As the malware uses advanced fileless techniques it flew under the radar, making it difficult for traditional signature-based antivirus solutions to detect it.
Defending against Novter with DNS Filtering
The simplest solution for IT and management is a DNS-based web content filtering system. Such a system will block users from accessing sites that contain malicious HTA files based on a content policy set up by administrators. DNS-based web content filters are superior to older systems that simply checked the domain name against a list of restricted sites. Instead, a user is unable to access or download content based on a list of policies set up to block during the process of DNS lookup.
Simple web content filters had backdoors and ways around filters, but DNS-based filters can’t be avoided due to the nature of the way the Internet works. Every time the user clicks a link or types a domain into a browser, a DNS query is performed. During the lookup process, a system such as WebTitan Cloud performs an additional lookup on the network web content policy. Policies can be set on specific domains and their associated IP addresses, but network administrators can also categorize searches and block inappropriate content. The user is given a message that their access to the site was blocked, and administrators receive notifications that a site within the policy was queried.
DNS is not just used in browser queries where the user types a domain name into the address bar. DNS is also used in other applications even in the background for services that use the Internet. Fileless attacks use in-memory applications already available on the local device, so a DNS-based web content filter would block any attacks that utilize these local tools to access malicious sites. Any process that requires DNS (which is any Internet-based request) would be blocked by the web content filters.
With cloud-based filters, the organization does not need expensive equipment to host the system. Administrators tie local DNS into the cloud-based filters where all processing, notifications, and logging run. You might be interested to read a recent article discussing the top 6 reasons DNS Security is faster and better at killing attacks.
Malware creators continue to create new ways to evade detection, and fileless attacks are the latest trend that could lead to large breaches in 2020. Thousands of endpoints in both the US and Europe have been infected by this fileless malware in the past few weeks. By focusing on reducing the attack surface, this threat can be mitigated with robust security controls. Organizations can get ahead of these attacks by implementing DNS-based filters like WebTitan which detects malicious files, scripts, as well as blocking access to malicious URLs.
Why not try WebTitan Cloud for free and see for yourself?

Talk to our Team today



