Hardware firewalls provide essential security for almost all TCP/IP networks. Whether it’s small business networks or large enterprise environments, a network firewall controls traffic flowing between the external public internet and the internal environment. Most corporate networks have an expanded design beyond an internal environment, including intranets on internal network zones, untrusted demilitarized zones (DMZ), and other optional intermediate security zones. Corporate networks with services at the perimeter need a firewall to allow legitimate traffic to access them while keeping the public internet from sending malicious traffic intended to steal data or compromise a system.
A security zone is a network segment that hosts a group of systems with similar functionality open to the public internet but outside the internal network. It requires security, but intrusion detection and monitoring should be set up to allow public internet access. For example, a web server should be available to the public internet, but this traffic should not pass firewalls to the internal network. These firewalls are called layer 3 firewalls as they identify traffic request IP addresses and ports and block or allow them depending on access rules.
Some firewalls work on layer 7 of the OSI model. Layer 7 firewalls control authorized traffic on the application layer, evaluating input sent to various internal services such as a database or a web server. For example, suppose you have an application firewall that protects the database from a public-facing web server. When users send input to the web server, the web server then sends the input to the database. An application firewall analyzes information for malformed input such as cross-site scripting (XSS) or SQL injection (SQLi) and rejects it if the input contains malformed commands.
What is the Network Perimeter?
The components included in a network perimeter depend on your infrastructure design, business rules, and technology budget. A few components are usually included in an enterprise network perimeter:
- Routers: Routers and switches control the flow of traffic and segment the network into logical environments. They act as the traffic control component for any network traffic and direct authorized traffic to the right network segment. For example, a router directs web page requests to the network segment hosting a business web server.
- Firewalls: Routers and firewalls work together to determine if traffic is allowed to access a network segment. Firewalls block or allow traffic based on administrator configurations on the device, and they log traffic to determine if malicious unauthorized traffic access the network.
- Intrusion Detection System (IDS): Administrators need a way to detect when malicious traffic accesses the network or threats attempt to launch an attack against the network. An IDS alerts administrator when suspicious activity is detected so that they can review it further.
- Intrusion Prevention System (IPS): An IDS usually works together with an IPS. An IPS is more active and works to prevent malicious traffic from accessing the network. Instead of alerting administrators of malicious unauthorized access, an IPS stops malicious activity from happening, contains it, and alerts administrators that traffic was successfully blocked.
- Demilitarized Zone (DMZ): A DMZ is a network segment containing servers and infrastructure available to the public. It’s outside the internal network but within the perimeter. For example, a public web server hosted on-premises should be in the DMZ.
You could have one or none of these components in your network design, but it’s likely that you have at least a router and firewall. If you host all your applications and services in the cloud, then you might not have a DMZ, but the cloud provider has infrastructure for a network perimeter so that you can set up monitoring and detection with an IDS and IPS.
Perimeter Security Zone Segmentation for Enterprise Networks
Every enterprise network has its unique environment. A security zone network segment will look different from business to business, depending on services in the DMZ and user permissions connecting from a remote location.
Even with unique requirements, organizations should still follow best practices. A “best practice” approach to implementing a network perimeter offers enhanced security and data protection from common cybersecurity attacks. A general best practice approach is illustrated in the diagram below. Again, the network topology in the image is an example and might differ from your own. Every organization will have variations from the example design, such as using two firewalls instead of one or only one DMZ instead of two. A firewall in every DMZ protects the internal corporate environments from the public internet. In some designs, two firewalls protect the DMZ and internal network from the public internet.
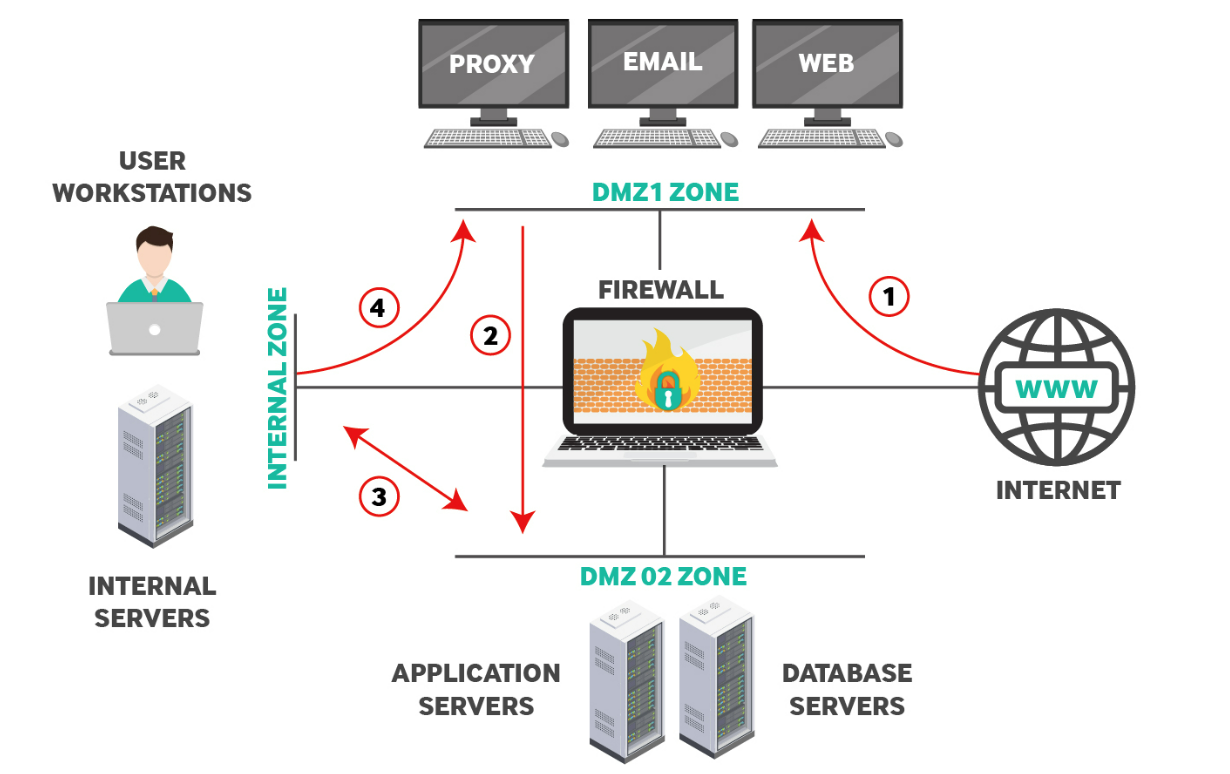
The perimeter network above includes two DMZs (Demilitarized Zones), DMZ1 and DMZ2, and an Internal zone for authorized users only. The red lines with arrows indicate the authorized traffic flow to and from the firewall. Notice that the public internet can only access one DMZ, which is common when corporations host their servers and internal applications available to the public (e.g., a web server or communication channel).
A DMZ zone is commonly open to the public internet and internal users, so it’s considered partially secure. Traffic should never flow directly from the DMZ to the internal network. Any internet-accessible services should always be in the DMZ where internal users can access them.
Why Have a DMZ Zone?
A DMZ zone is an isolated subnet on which connected hosts are usually exposed to the public internet to provide services to users, such as web applications, email communications, and DNS services. DMZ environments are the most vulnerable to cybersecurity attacks, as these zones take input from the public internet and allow access to services from internet users. Because of the increased cyber risks associated with a DMZ, its security is maximized to limit damage should one of these servers be compromised. The strategy contains a compromised server within the DMZ, so internal applications are protected from data exfiltration, malware, ransomware, and eavesdropping.
A DMZ is necessary if an organization hosts any application that is available on the public-facing internet. Usually, DMZs are reserved for organizations using on-premises services, but a security engineer might set up a DMZ in a hybrid cloud environment, too. Organizations with cloud-hosted services have their own form of DMZ, especially when hosting shared services between employees and the public internet. Setting up a DMZ correctly often requires professional help and penetration testing.
DMZ1 – Publicly Available Applications
This zone hosts the public-facing servers that must be accessible from the Internet. It usually hosts services such as Web, Email, DNS, Proxy, etc. The firewall should allow traffic from the Internet towards DMZ1 only (see Traffic Line 1 above). Also, only the required TCP/UDP ports must be allowed (such as 80, 443, 25, etc.). This network segment should be monitored heavily for any malicious traffic.
DMZ2 – Intermediary Between Internal and External Networks
DMZ2, on the diagram, is an intermediary zone set up to host application servers, database servers, and other services available to both the public internet and internal employees. DMZ2 acts as an intermediary between public users and public services (e.g., web or email) to protect the internal environment from the public internet. Creating an additional step from the public internet to DMZ2 reduces risks from a compromise and cybersecurity event. For example, a threat might compromise a service on DMZ1, but it still must compromise another security layer before reaching the internal environment.
Some enterprise environments have a public-facing web server and web-based application dedicated to employee productivity. For example, a web-based business customer service application might pull data from a publicly available web application. In this example, the front-end public web server should communicate with a web application server in a separate security zone. The example diagram has a web application in DMZ1 and an employee-accessible web server in DMZ2.
Security experts suggest that a web application sending and receiving data on a database must not be installed on the same physical machine as the database server. Separating physical devices adds a layer of security, requiring cyber-attackers to compromise two separate environments, which reduces risks. The added layer also increases the chance that intrusion protection services will detect anomalous behavior and alert administrators before both machines can be compromised. Mitigating risks is the primary goal for security infrastructure, and no environment is completely protected against all cyber threats.
The above arrangement protects the internal private network since any compromise of the database or application servers via the DMZ1 servers will not result in access to the protected internal network. Network security always works in layers; the two DMZ environments add these layers to the protected internal environment.
In the diagrammed example, the firewall is configured to only allow access to DMZ2 from DMZ1 on authorized ports indicated by the red line labeled “2.” Also, DMZ2 has limited access to and from the internal zone, indicated by the red line “3.” Traffic flow from the internal network to DMZ2 is set for exceptional cases, such as accessing an internal management server, automated backup procedures, or authentication services on an Active Directory server. All these exceptional cases are examples, but an enterprise environment might have these scenarios or more when firewalls are configured between DMZ environments.
Internal Security Zone
This zone usually hosts internal user workstations and critical servers such as file servers, Active Directory servers, internal databases, specialized applications (e.g., sales or accounting software), and other business software. The firewall must not allow direct access from the internet to this Internal network.
Outgoing web traffic from users in this network can access the Internet using an HTTP proxy server (see Traffic Line 4) located in DMZ1. Companies can implement countless network perimeter environments to facilitate their business productivity. The discussion above suggests a solid firewall zone segmentation to achieve strong network security in an enterprise environment.
A Few Other Firewall Configuration Best Practices
The example diagram won’t represent every enterprise network, but it’s a basic overview of a network with security best practices in place. Here are a few best practices you can incorporate into your own firewall configurations and infrastructure design:
- Store Audit Logs: Logs are necessary for investigations and analysts to detect suspicious behavior. Keep logs based on your retention plan to support incident response after a cyber event.
- Default Deny: It’s better to allow traffic rather than allow all traffic by default except on specific ports. Set firewalls to allow only traffic necessary for business services.
- Label Everything: Firewalls allow administrators to label rules, which helps other administrators understand traffic flow. Labeling rules also avoid configuration mistakes that could be detrimental to the security of your environment.
- Secure Administrator Accounts: Use strong passwords on accounts with permission to change firewall settings and rotate passwords and keys regularly to reduce the window of opportunity during an account compromise.
- Always Test Configurations: Before deploying a firewall to production, test settings and ensure traffic flow is as expected.
- Keep Firmware Patched: Security patches are essential to the security of your environment, and developers deploy firmware updates to address specific security vulnerabilities. By keeping firewalls updated, it patches known vulnerabilities that could threaten the integrity of your entire environment.
- Regularly Audit Firewall Configurations: Changes can occur even after testing a firewall before deployment to production. Administrators should devise a plan to periodically audit firewall settings to ensure that no new changes alter the security of their network environment.
- Configure Firewalls Using the Least Privilege Principle: The least privilege principle says users should only have access to data necessary to perform their job function. Firewall configurations should follow this strategy to avoid an overly permissive traffic flow, which could lead to an unexpected system compromise.
- Use a Change Management Plan: Firewall changes affect traffic flow, negatively impacting security, network availability, and integrity. Design a change management plan to determine the best time of day to deploy changes and warn users that the change may impact application availability.
- Have a Rollback Plan: If changes or a firewall negatively impact network availability after deployment, have a rollback plan ready to return the network to its initial state, significantly if changes negatively affect security.
- Automate Repeatable Tasks: Administrators using automation are much less likely to make mistakes, so automate repeatable tasks when possible.
Read TitanHQs Complete Network Security Checklist
Get Started With TitanHQs DNS Filtering Solution
Web content filtering is a cybersecurity layer that should be included in any environment where external access is provided to employees, contractors, vendors, and other third parties. It blocks many common threats, including ransomware, malware, phishing, and credential theft. Users are any organization’s weakest link, and malware and ransomware often lead to critical data breaches.
Talk to our Team Today

